Articles worth reading
Press-release

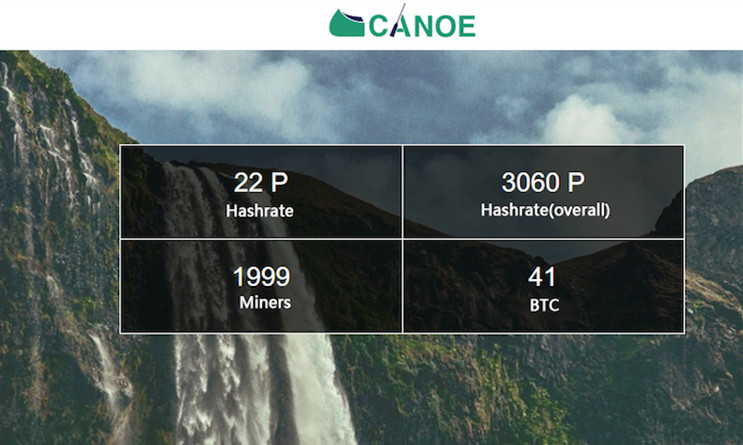
Mining
Technologies
Reviews
Interview

Summary of Chinese articles that support softfork scaling
Ma Long, or better known as Maya/Cndx in Chinese Bitcoin community, is a S...

BTC38 to Offer 0% Transaction Fee for Company Account
On 5th Dec, BTC38 introduced company account verification and 0% transactio...

Joint-interview: on Collaboration between WINGS and China’s Antshare
When it comes to bitcoin and blockchain technology, China and Western commun...
Qtum Introduce Master Contract and ID Identification Option into Blockchain
The Qtum open-source community released its whitepaper: Value Transfer Ne...
8btc English News (news.8btc.com) is set to bridge the blockchain development between China and abroad. The development of Chinese blockchain industry will be updated regularly to help the Chinese blockchain startups to gain access to the overseas market. Also 8btc is seeking to help foreign blockchain-related projects to grow their business and community in China.
 English
English
 Chinese
Chinese